Want a heads up when a new story drops? Subscribe here.
Standard risk mitigation strategies and approaches are not designed with social media in mind. Businesses suffer brand reputation damage, stock markets witnessed fraudulent postings, and financial service providers have been forced to erase their social media presence due to negative feedback.
Networking sites offer a plethora of benefits for brands in terms of visibility, communication, and customer reach. At the same time, they are faced with many financial, reputational, safety, and compliance risks.

There is always a risk of something going wrong because of the number of people involved in social media marketing, the number of communication channels used, or the volume of information shared and managed. Whether it is overwhelming followers with long or tedious posts or data leakage, risks occur in many ways.
To prevent this scenario from happening, it is important to develop social media risk mitigation strategies with a focus on content control, malware, compliance, and employees wasting company time.
Table of Contents
Malware and Hacker Attacks

Companies face a multitude of social media risks but it appears that malware is one of the problems that worry marketers the most. A 2020 survey involving 600 senior IT and security professionals reveals that malware is a concern for 69 percent of respondents, followed by data loss (59 percent), account compromise (50 percent), and infiltration (42 percent). That malware attacks worry businesses is not surprising. Hackers can cause huge reputation damage by gaining access to social media accounts.

Giannis Antetokounmpo
In 2020, for example, hackers gained access to NBA MVP Giannis Antetokounmpo’s bank, email, phone, and social media accounts. The tweets included racial slurs, inappropriate language, and a claim that the player tested positive for Covid-19. Even when the messages got deleted, some media outlets kept posting screenshots to cover the story. (Ekathimerini).
Fifteen NFL teams also got their Instagram, Facebook, and Twitter accounts hacked in 2020, and the group OurMine claimed responsibility for the hacks. Their banners and profile photos disappeared, with strange messages being tweeted out (Insider). While these cyberattacks are relatively benign, they still caused reputation damage and hassle for the players involved.
And it isn’t only major league players that cybercriminals are targeting. A 2019 survey by Statista shows that 19 percent of businesses worldwide were targets of 11 – 25 attacks and 33 percent of companies of 1 to 10 cyberattacks. Obviously, businesses should be vigilant in their safety and security efforts to protect their social media accounts. One way to minimize risk is to always use a private WI-FI network that adds an extra level of security.

Hackers can and do create fake networks to steal sensitive information. For example, if employees use business devices in McDonald’s and join a fake McDonalds Guest network, their work and social media accounts will be accessible to cybercriminals.
Many hackers also create social media profiles to steal information. To prevent identity theft and fraudulent account activity, it is important to confirm the identity of users sending friend requests. Most social media networks have a way of showing whether an account is verified or not. Tweeter, for example, adds a blue checkmark to verified accounts such as Office Small Biz, 10K Small Entrepreneur, and Google Small Biz.
Content Control

Everyone makes mistakes but some mistakes can cause significant reputational damage, resulting in the loss of market share and social and financial capital. Disrespectful language and insensitive comments by employees should never be tolerated, including offending users and posting defamatory statements and incorrect information.
Consider the following two examples. A customer who didn’t like the pumpkin pie at Marc Orfaly’s restaurant in Boston complained about the restaurant’s Facebook page. The manager/chef unloaded on her by posting: “Judging by how fat your face looks, you most likely shouldn’t be eating any more desserts” (Neilpatel).

The Twitter account of StubHub posted a message saying “Can’t wait to get out of this stubsucking hell hole” (Pingler). It is not clear whether that was a disgruntled employee or someone who had hacked the account, but it is an example of a message that can ruin a company’s reputation.
In some cases, social media risks happen over disputes over the use of a brand’s name. Nike has recently taken court actions against the creative collective MSCHF over their collaboration with Lil Nas X on the Satan Shoes- made using Nike Air Max 97s. The pair of sneakers caused a controversy among religious groups. Nike claims it has nothing to do with the creation of the shoes has taken legal actions in an attempt to distance the brand from the sneakers.
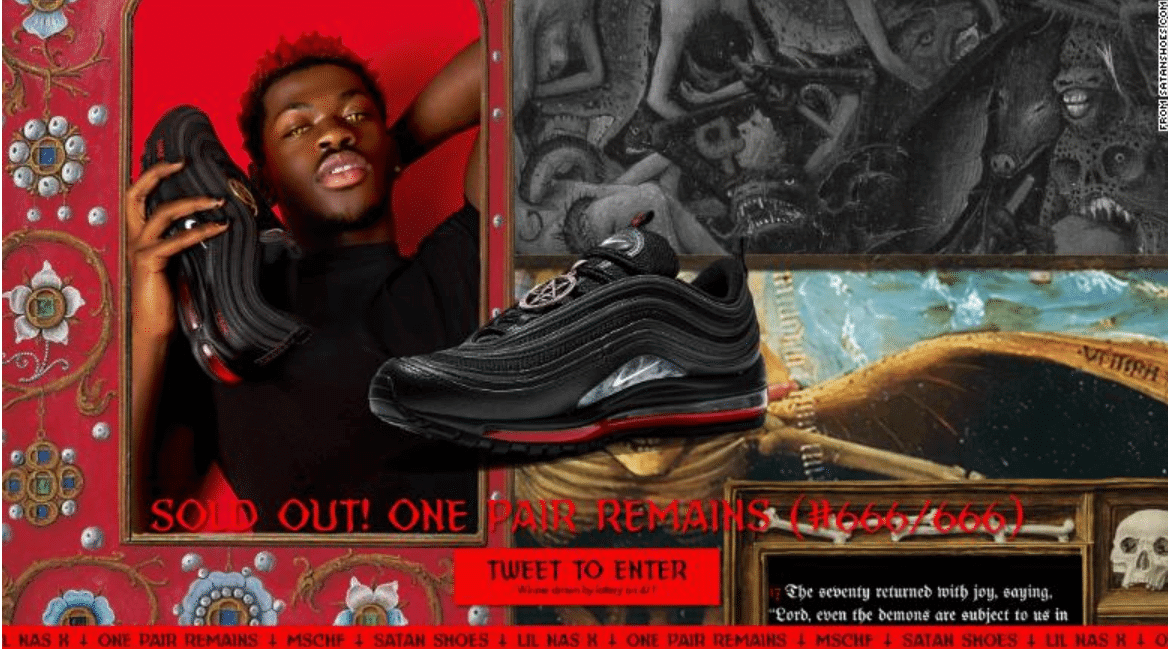
Lil Nas X with the Satan Shoes
In addition to using inappropriate or disrespectful language, other risks include information overload, loss of quality, disclosure of confidential information, and outdated content. Loss of quality refers to posting messages that are short and less comprehensible, sharing irrelevant content, and posts that are useless for the company itself or customers.

Loss of privacy or exposure of personal information occurs when information shared on social media results in unwanted exposure. This can be attitudes, product preferences, date of birth, or job position.
To keep control over the content, it is important to provide team members with social media guidelines covering details like language, grammar, tone of voice, and formatting. This will help ensure that everyone’s tone of voice is on the same page.
Additionally, team members should be able to answer basic questions such as: What do you stand for? What makes you unique? What are your promise and purpose? Who are your competitors? Inconsistent answers to these questions could spell trouble for your social media content marketing efforts.
Compliance

This risk category includes failure to comply with various industry regulations and laws such as data protection, privacy, third-party liability, and breach of confidentiality. Compliance risk can result in material loss, financial forfeiture, and legal penalties. Breach of confidentiality, for example, refers to disclosure of know-how, trade secrets, and confidential information. As employees discuss all sorts of topics online, outside and during work hours, data can leak and result in material loss or reputation damage.
This can happen when employees share information about upcoming products, technologies in use, or internal email addresses. Other types of leaks occur when people share their personal phone numbers, vacation or travel plans, personal life, and other non-business information. Such oversharing puts both employers and employees at risk and aids criminals looking to breach businesses.

Copyright infringement can also result in criminal and civil penalties. It involves sharing content such as writing, music, and photos protected by law without having use rights. One example of copyright infringement is where a customer purchases a product and shares a post discussing its benefits. The author of the post is the first owner of the copyright. The company offering this product can repost the article only after obtaining the author’s permission. Publishing without consent could subject the company to liability for copyright infringement.
Additionally, social media use can implicate legal issues such as advertising and marketing regulations, defamation, and workplace discrimination and harassment. To minimize compliance risk, businesses need to incorporate social media use clauses into their internal guidelines, procedures, and policies. It is also the duty of employers and senior-level managers to supervise their employees while handling company accounts.
Employees Wasting Company Time

Social media can be a competitive advantage. But it can also be addictive and disruptive when employees spend too much time on it. This can result in a loss of productivity in the workplace. Indeed, a Pew Research Center survey found that employees mainly use social media for non-work purposes. More than 1/3 of the respondents or 34 percent use networking sites to take a mental break from work while 27 percent use social media to connect with family and friends. Only 12 percent of people say they use networking sites to ask work-related questions to persons inside their company.
One way to limit social media use at work is to develop a formal policy or code of conduct and notify employees that the company has the right to monitor use. Another way to go about this is to block access to networking sites on company-owned electronic devices and computers. This can be a good alternative for larger organizations that lack the human resource to monitor social media use.
Summing Up

Social media has changed the way brands engage with customers and promote their business. If it is not managed properly, however, social media can open companies up to significant reputational, legal, and financial risks. To prevent this scenario and keep abreast of exposure, businesses must develop sound social media risk mitigation strategies. Brands can effectively manage compliance risk by staying current on changing regulations and laws in areas such as defamation, disclosure, and confidentiality. Some companies also opt for additional coverage such as media liability insurance. Second, it is important to incorporate social media clauses into internal policies and guidelines. Examples include clauses on workplace social media use and guidelines for creating content. Finally, businesses should be vigilant in their security efforts to avoid getting hacked and secure their social media accounts.
A broader approach to mitigation involves risk identification, description, and categorization. This approach allows companies to determine whether risk originates from technical or human causes. Focusing on the root of the problem enhances overall safety and security, content quality, and social media communications.